Firewall technology will undergo major changes as we approach the introduction of 5G across industries.
Service Providers will have to secure services across 2G/3G, 4G and 5G for many years to come. In conjunction with the introduction of IT protocol in the 5G mobile core, security solutions such as the SS7 firewall require a fundamentally different and converged approach.
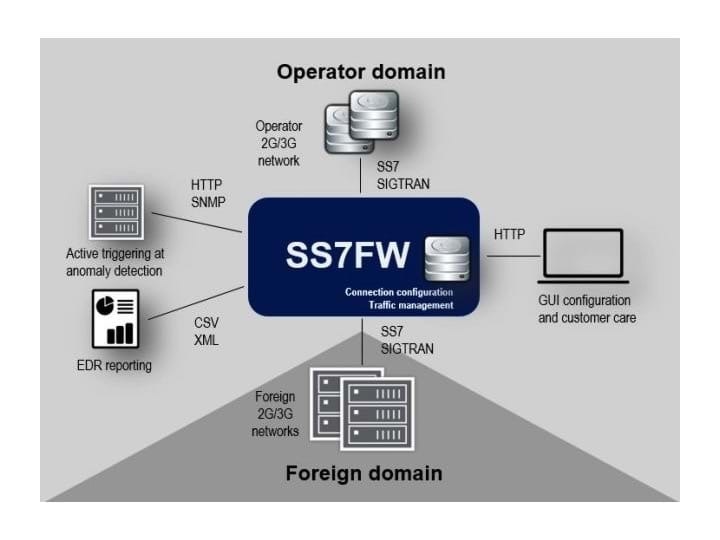
What is the SS7 firewall?
The SS7 firewall is a ‘signalling firewall’ used to protect mobile operators from SS7 Attacks. The SS7 firewall protects legacy networks (SS7 based) specifically against potential attacks, unauthorised senders, malformed messages, stolen mobile identities and much more. The SS7 Firewall supports the FS.11 GSMA guidelines for signalling firewalls of the SS7 protocol.
The SS7 firewall is a single-engine software solution designed to work across signalling protocols, such as Diameter, HTTP/2, SS7, and more. Nomios considers a threat to one domain as a threat to all domains. That’s why the signalling firewall provides service providers with a path to gradual migration and centralised security architecture across Diameter, SS7 and HTTP/2 – required for 5G signalling operations.
5G security and SS7 firewall functionality across access networks
Because of the technical flaw found in SS7 – one of the biggest infrastructure loopholes in the telecom web which has become a source of fear and paranoia, the SS7 firewall is getting more and more attention from the telecom and service provider industry.
It shows that the traditional approach to securing signalling per access technology (and protocol) no longer suffices. Security products are commonly designed on the assumption that securing a single protocol technology is sufficient. Never before were mobile networks so vulnerable to attacks from the connected world, making 5G security an essential element for your 5G Transition and thus Mobile Solutions.
The telecom industry has to rethink how to deal with these new threats. Mobile network technologies and the protocols supporting them evolve rapidly and so do the criminals looking for ways to exploit them.
Related solutions
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.